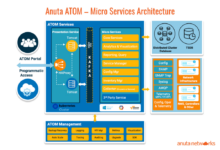
Secure Cloud Networking Solutions: The Key to Protecting Your Cloud Environment
As Secure cloud networking solutions take center stage, this opening passage beckons readers into a world crafted with good knowledge, ensuring a reading experience that is both absorbing and distinctly original. With the increasing adoption of cloud computing, organizations are faced with the challenge of securing their cloud networks to protect sensitive data and applications.
This comprehensive guide delves into the fundamentals of secure cloud networking, providing best practices, industry-specific solutions, and emerging trends to help organizations navigate the complexities of cloud security.
Secure cloud networking involves implementing a combination of security measures, including network segmentation, encryption, access control, and intrusion detection systems, to protect cloud networks from unauthorized access, data breaches, and other security threats. By understanding the key concepts and best practices of secure cloud networking, organizations can effectively safeguard their cloud environments and ensure the confidentiality, integrity, and availability of their data and applications.
Network Security Fundamentals
A secure cloud network is a virtual network that is designed to protect data and applications from unauthorized access. It uses a variety of security measures, such as firewalls, intrusion detection systems, and encryption, to protect against threats such as malware, hacking, and data breaches.
Network security is essential in cloud environments because it helps to protect data and applications from a variety of threats. These threats can include:
- Malware: Malware is a type of software that is designed to damage or disable computer systems. It can be spread through email attachments, downloads, or malicious websites.
- Hacking: Hacking is the act of gaining unauthorized access to a computer system or network. Hackers can use a variety of techniques to gain access to systems, including phishing, brute force attacks, and social engineering.
- Data breaches: A data breach is an incident in which sensitive data is accessed or stolen by unauthorized individuals. Data breaches can be caused by a variety of factors, including hacking, malware, and human error.
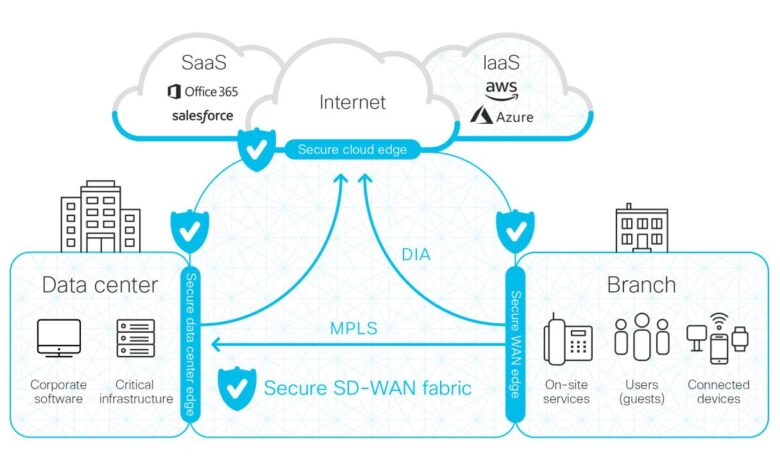
Cloud Network Architecture
Cloud network architecture refers to the design and implementation of networks within cloud computing environments. It involves the creation, configuration, and management of virtual networks and the underlying infrastructure that supports them. Cloud network architectures can vary depending on the specific requirements and use cases of an organization.
Cloud Network Architecture Types
There are several common cloud network architectures, including:
- Hub-and-Spoke:In this architecture, a central hub connects to multiple spokes, which are typically virtual private clouds (VPCs). The hub provides connectivity between the spokes and to external networks, while the spokes provide isolation and security for individual workloads.
- Virtual Private Cloud (VPC):A VPC is a private network within a cloud provider’s infrastructure. It provides isolation and security for workloads running in the cloud, and it can be configured to connect to other VPCs or on-premises networks.
- Software-Defined Networking (SDN):SDN is a network architecture that uses software to control and manage network devices and resources. It provides flexibility and programmability, allowing organizations to automate network configuration and management tasks.
Secure Cloud Network Design
Secure cloud network design involves implementing best practices to protect cloud-based networks from unauthorized access, data breaches, and other security threats. By following these best practices, organizations can ensure the confidentiality, integrity, and availability of their cloud-based data and applications.
Some of the best practices for designing secure cloud networks include:
- Segmentation:Divide the network into multiple segments to limit the impact of a security breach. Each segment should be assigned a unique security policy that defines the level of access and protection required.
- Encryption:Encrypt data at rest and in transit to protect it from unauthorized access. Encryption keys should be managed securely and regularly rotated.
- Firewalls:Implement firewalls to control access to the network and prevent unauthorized traffic from entering or leaving.
- Intrusion detection and prevention systems (IDS/IPS):Monitor network traffic for suspicious activity and take action to block or mitigate attacks.
- Regular security audits:Regularly audit the network to identify and address any security vulnerabilities.
By following these best practices, organizations can design and implement secure cloud networks that protect their data and applications from a wide range of threats.
Common Cloud Network Security Risks
There are a number of common security risks that can affect cloud networks. These risks include:
- Unauthorized access:Unauthorized users may gain access to the network and its resources, potentially leading to data breaches or other security incidents.
- Data breaches:Data breaches can occur when sensitive data is accessed or stolen by unauthorized users.
- Denial of service (DoS) attacks:DoS attacks can prevent authorized users from accessing the network or its resources.
- Malware:Malware can infect cloud-based systems and steal data, disrupt operations, or launch other attacks.
- Insider threats:Insider threats occur when authorized users misuse their access to the network or its resources.
Organizations can mitigate these risks by implementing a comprehensive security strategy that includes the best practices described above.
Cloud Network Security Monitoring and Alerting
Cloud network security monitoring and alerting is essential for detecting and responding to security threats. Organizations should implement a monitoring system that collects and analyzes data from a variety of sources, including network traffic, security logs, and system events. This data can be used to identify suspicious activity and trigger alerts that notify security personnel of potential threats.
Organizations should also develop a response plan that Artikels the steps to be taken in the event of a security incident. This plan should include procedures for isolating affected systems, containing the damage, and restoring normal operations.
Real-World Case Studies
There are a number of real-world case studies that demonstrate the benefits of secure cloud network design. For example, a major financial institution implemented a cloud-based network that was designed to meet the highest security standards. The network included multiple layers of security, including segmentation, encryption, and firewalls.
As a result, the financial institution was able to protect its data and applications from a number of security threats, including a major DDoS attack.
Another example is a healthcare provider that implemented a cloud-based network to store and share patient data. The network was designed to meet HIPAA security standards and included a number of security features, such as encryption, access controls, and intrusion detection.
As a result, the healthcare provider was able to protect patient data from unauthorized access and other security threats.
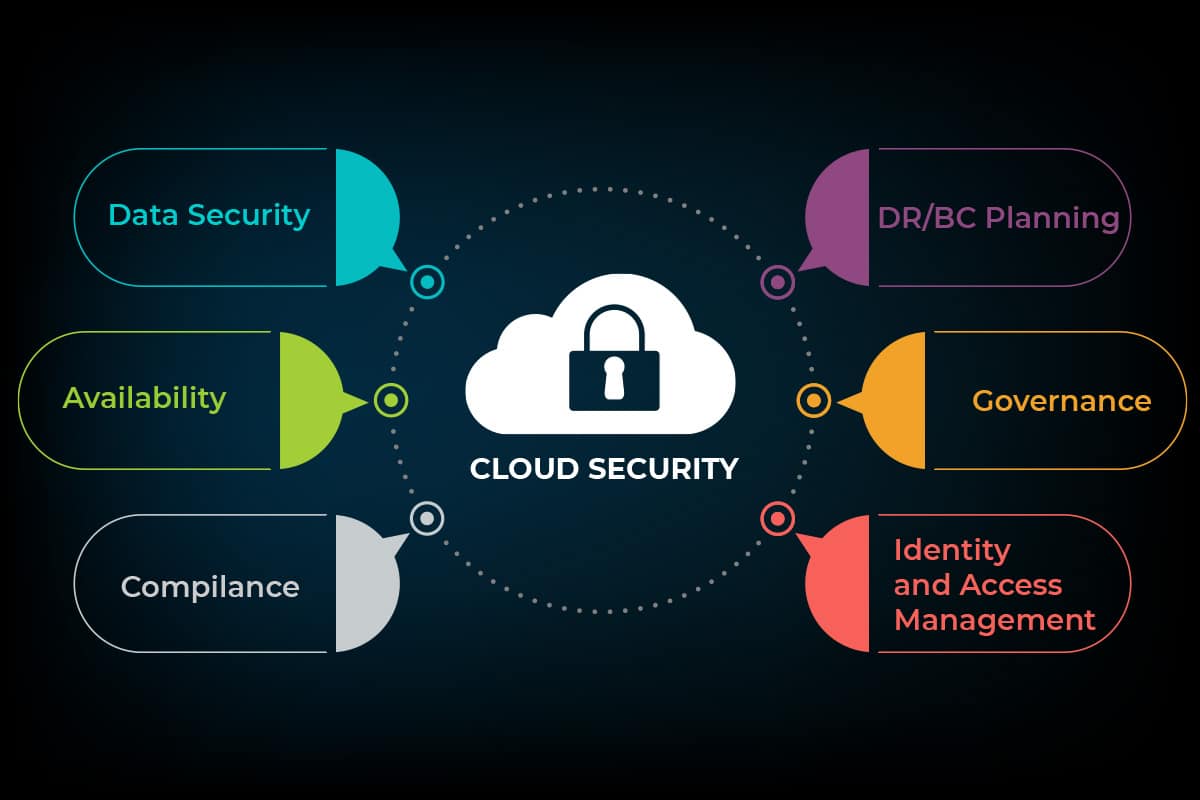
Key Security Considerations for Cloud Network Design
| Security Consideration | Description |
|---|---|
| Segmentation | Divide the network into multiple segments to limit the impact of a security breach. |
| Encryption | Encrypt data at rest and in transit to protect it from unauthorized access. |
| Firewalls | Implement firewalls to control access to the network and prevent unauthorized traffic from entering or leaving. |
| Intrusion detection and prevention systems (IDS/IPS) | Monitor network traffic for suspicious activity and take action to block or mitigate attacks. |
| Regular security audits | Regularly audit the network to identify and address any security vulnerabilities. |
Flowchart for Designing a Secure Cloud Network
[Insert flowchart here]
Code Snippet for Implementing Network Segmentation in a Cloud Environment
# Create a new network
network = client.create_network(
project=project_id,
network_id="my-network",
body=
"name": "my-network",
"auto_create_subnetworks": False,
,
)
# Create a new subnet
subnet = client.create_subnetwork(
project=project_id,
region=region,
subnet_id="my-subnet",
body=
"name": "my-subnet",
"network": network.name,
"ip_cidr_range": "10.0.0.0/24",
"region": region,
,
)
Security Policy for a Cloud Network
A security policy defines the rules that govern traffic flow within a cloud network.
A well-defined security policy can help to protect the network from unauthorized access and other security threats.
The following is an example of a security policy for a cloud network:
- Ingress rules:Ingress rules define the traffic that is allowed to enter the network. For example, an ingress rule could allow traffic from a specific IP address or range of IP addresses.
- Egress rules:Egress rules define the traffic that is allowed to leave the network. For example, an egress rule could allow traffic to a specific IP address or range of IP addresses.
- Target tags:Target tags can be used to group resources within the network. For example, a target tag could be used to identify all of the web servers in the network.
- Service accounts:Service accounts can be used to grant access to resources within the network. For example, a service account could be used to grant access to a specific web server.
By defining a clear and concise security policy, organizations can help to protect their cloud networks from a wide range of security threats.
Checklist for Auditing the Security of a Cloud Network
- Review the network configuration to ensure that it is in compliance with security best practices.
- Check for any unauthorized access to the network.
- Review the security logs to identify any suspicious activity.
- Test the network’s security controls to ensure that they are working properly.
- Conduct regular security audits to identify and address any security vulnerabilities.
By following these steps, organizations can help to ensure that their cloud networks are secure and protected from a wide range of threats.
Cloud Network Management

Effective management of cloud networks is crucial for maintaining network performance, security, and compliance. Cloud network management encompasses the monitoring, troubleshooting, and optimization of virtual networks, ensuring seamless connectivity and data flow within the cloud environment.
Tools and techniques for cloud network management include:
- Network monitoring tools: Provide real-time visibility into network traffic, performance, and health.
- Configuration management tools: Automate network configuration and changes, ensuring consistency and reducing errors.
- Security management tools: Monitor and enforce network security policies, detecting and mitigating threats.
- Performance optimization tools: Analyze network performance, identify bottlenecks, and optimize traffic flow.
- Cloud management platforms: Provide a centralized view and control over cloud resources, including networks.
Cloud Network Monitoring
Monitoring cloud networks is crucial for ensuring optimal performance, security, and compliance. By leveraging logs, metrics, and other monitoring tools, organizations can gain visibility into their cloud networks and proactively address potential issues.
Logs provide a detailed record of events and activities within the network, while metrics offer real-time insights into key performance indicators such as bandwidth utilization, latency, and packet loss.
Best Practices for Monitoring Cloud Networks
- Establish clear monitoring goals and objectives.
- Use a combination of logs, metrics, and other tools for comprehensive monitoring.
- Configure alerts and notifications to promptly notify of network issues.
- Monitor network performance regularly to identify trends and anomalies.
- Review logs and metrics periodically to identify potential security threats.
Monitoring Tools
| Tool | Advantages | Disadvantages |
|---|---|---|
| Cloud Monitoring |
|
|
| Third-party Monitoring Tools |
|
|
| Open Source Monitoring Tools |
|
|
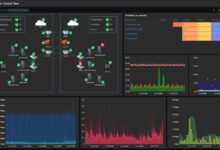
Sample Monitoring Dashboard for a Cloud Network
A sample monitoring dashboard for a cloud network might include the following metrics:
- Network traffic (ingress and egress)
- Packet loss
- Latency
- CPU and memory utilization of network devices
- Security events
Alerts and Notifications, Secure cloud networking solutions
Alerts and notifications are essential for promptly notifying of network issues. These can be configured based on specific thresholds or conditions. For example, an alert can be triggered if network traffic exceeds a certain threshold or if a security event is detected.
Importance of Monitoring Network Performance for Security and Compliance
Monitoring network performance is critical for maintaining security and compliance. By identifying potential issues early on, organizations can prevent or mitigate security breaches and ensure compliance with regulatory requirements.
End of Discussion: Secure Cloud Networking Solutions
In conclusion, secure cloud networking solutions are essential for organizations to protect their cloud environments and maintain compliance with industry regulations. By implementing a comprehensive security strategy that incorporates best practices, industry-specific solutions, and emerging technologies, organizations can effectively mitigate security risks, ensure the confidentiality and integrity of their data, and drive innovation in the cloud.