Advanced Cloud Networking Security Protocols: Securing Your Cloud Networks
Advanced cloud networking security protocols are essential for protecting your cloud-based applications and data. These protocols provide a comprehensive range of security measures, including encryption, authentication, and access control. In this guide, we’ll explore the different types of advanced cloud networking security protocols, their benefits, and how to implement them effectively.
As cloud computing continues to grow in popularity, so does the need for robust security measures. Advanced cloud networking security protocols are a key part of any cloud security strategy, providing a comprehensive approach to protecting your cloud-based assets.
Advanced Cloud Networking Security Protocols
Advanced cloud networking security protocols are a set of security measures designed to protect cloud-based networks from unauthorized access, data breaches, and other security threats. These protocols provide a comprehensive approach to network security, encompassing both traditional and cloud-specific security mechanisms.
Fundamental Principles
The fundamental principles of advanced cloud networking security protocols include:
- Confidentiality:Ensuring that data is only accessible to authorized users.
- Integrity:Protecting data from unauthorized modification or corruption.
- Availability:Ensuring that data and network resources are accessible when needed.
- Authentication:Verifying the identity of users and devices.
- Authorization:Granting or denying access to resources based on user roles and permissions.
Types of Advanced Cloud Networking Security Protocols
Advanced cloud networking security protocols provide robust protection for cloud-based networks. These protocols employ sophisticated mechanisms to safeguard data and ensure network integrity. Understanding the different types of advanced cloud networking security protocols is essential for selecting the appropriate measures to secure your cloud infrastructure.
Transport Layer Security (TLS)
TLS is a widely adopted protocol that establishes secure communication channels between clients and servers. It utilizes encryption and authentication mechanisms to protect data in transit, preventing eavesdropping and data manipulation.
Secure Sockets Layer (SSL)
SSL is a predecessor of TLS that provides similar functionality. It secures communication channels and protects data transmission, ensuring the confidentiality and integrity of sensitive information.
Internet Protocol Security (IPsec)
IPsec operates at the network layer, providing encryption and authentication for IP traffic. It secures communication between hosts and networks, protecting against unauthorized access and data interception.
Secure Shell (SSH), Advanced cloud networking security protocols
SSH is a secure remote access protocol that enables secure communication between two hosts over an unsecured network. It provides encryption, authentication, and data integrity, ensuring the confidentiality and integrity of remote access sessions.
Virtual Private Networks (VPNs)
VPNs create encrypted tunnels over public networks, allowing users to securely access private networks remotely. They provide confidentiality, integrity, and authentication, protecting data and network access from unauthorized entities.
| Protocol | Function | Key Features |
|---|---|---|
| TLS | Secure communication channels | Encryption, authentication, data integrity |
| SSL | Secure communication channels | Encryption, authentication, data integrity |
| IPsec | Secure network traffic | Encryption, authentication, data integrity |
| SSH | Secure remote access | Encryption, authentication, data integrity |
| VPNs | Secure remote network access | Encryption, authentication, data integrity |
– Provide a detailed explanation of the steps involved in implementing advanced cloud networking security protocols, including
Implementing advanced cloud networking security protocols involves a comprehensive process to safeguard cloud-based networks and data. The steps encompass:
Planning and Design
A well-defined plan and design lay the foundation for successful implementation. This phase includes:
- Identifying security objectives and risk assessment
- Selecting appropriate protocols based on security requirements
- Designing network architecture and topology
Protocol Selection and Configuration
Choosing the right protocols is crucial. Consider factors such as encryption strength, performance, and compatibility. Proper configuration ensures secure communication:
- Configure protocols with strong encryption algorithms
- Use certificates and key management systems for authentication
- Establish secure network configurations
Deployment and Testing
Deploy protocols according to the design and configuration. Thorough testing is essential:
- Test protocol functionality and connectivity
- Verify encryption and authentication mechanisms
- Monitor performance and identify potential bottlenecks
Monitoring and Management
Continuous monitoring and management ensure ongoing security:
- Monitor security logs and alerts for suspicious activities
- Perform regular security audits and vulnerability assessments
- Update and patch software and protocols as needed
Benefits of Advanced Cloud Networking Security Protocols
Advanced cloud networking security protocols offer a comprehensive suite of benefits that enhance cloud security and protect against evolving threats. These protocols provide improved visibility and control over cloud network traffic, enhancing protection against DDoS attacks, malware, and other malicious activities.
By leveraging encryption, authentication, authorization, intrusion detection, and prevention mechanisms, these protocols mitigate the risk of data breaches and compliance violations, ensuring the integrity and confidentiality of cloud-based data and applications.
Enhanced Visibility and Control
Advanced cloud networking security protocols provide granular visibility into cloud network traffic, enabling organizations to monitor and analyze network activity in real-time. This enhanced visibility allows for the identification of potential threats, performance bottlenecks, and compliance issues. By centralizing network security management, these protocols streamline operations and simplify the enforcement of security policies across multiple cloud environments.
Improved Threat Protection
Advanced cloud networking security protocols employ robust mechanisms to protect against a wide range of threats, including DDoS attacks, malware, and unauthorized access. Cloud-based firewalls, intrusion detection systems, and web application firewalls work in concert to identify and block malicious traffic, preventing data breaches and ensuring the availability of critical applications.
Reduced Risk of Data Breaches and Compliance Violations
By implementing advanced cloud networking security protocols, organizations can significantly reduce the risk of data breaches and compliance violations. These protocols enforce strict access controls, ensuring that only authorized users and devices can access sensitive data. Encryption mechanisms protect data in transit and at rest, minimizing the risk of unauthorized disclosure.
Additionally, these protocols provide comprehensive logging and reporting capabilities, enabling organizations to demonstrate compliance with regulatory requirements.
– Challenges of Advanced Cloud Networking Security Protocols
Advanced cloud networking security protocols offer robust protection, but their implementation and management can be complex. These protocols often require specialized expertise, extensive configuration, and ongoing monitoring, which can strain resources and increase operational costs.
Another challenge lies in the integration of these protocols with existing network infrastructure. Organizations must carefully plan and test the compatibility of advanced security protocols with their existing systems to avoid disruptions or security breaches.
Complexities and Limitations
The complexities of advanced cloud networking security protocols can stem from their underlying algorithms, encryption techniques, and key management mechanisms. These complexities can make it difficult for organizations to fully understand and implement the protocols effectively.
Additionally, some advanced protocols may have limitations in terms of performance, scalability, or compatibility with specific cloud platforms or applications. It is crucial for organizations to thoroughly evaluate the capabilities and limitations of these protocols before implementation.
Recommendations for Overcoming Challenges
- Partner with experienced cloud security vendors or consultants to gain expertise and support.
- Conduct thorough research and testing to ensure compatibility with existing infrastructure.
- Implement a comprehensive security strategy that aligns with business objectives and risk tolerance.
- Establish clear policies and procedures for managing and monitoring security protocols.
- Invest in training and education for IT staff to enhance their understanding and skills.
Emerging Trends in Advanced Cloud Networking Security Protocols
The field of advanced cloud networking security protocols is constantly evolving, with new protocols and technologies emerging all the time. These trends are shaping the future of cloud security, and it is important to be aware of them in order to stay ahead of the curve.
One of the most important trends in advanced cloud networking security protocols is the move towards zero trust. Zero trust is a security model that assumes that no one is trustworthy, not even those within the organization. This model requires that all users and devices be authenticated and authorized before they are granted access to any resources.
Another important trend is the adoption of artificial intelligence (AI) and machine learning (ML) in cloud security. AI and ML can be used to detect and respond to security threats in real time. This can help organizations to stay ahead of the curve and prevent attacks from causing damage.
Finally, there is a growing trend towards the use of cloud-native security solutions. Cloud-native security solutions are designed specifically for the cloud environment and can take advantage of the unique features of the cloud to provide enhanced security.
The Impact of Emerging Trends on Cloud Networking Security Practices
The emerging trends in advanced cloud networking security protocols are having a significant impact on cloud networking security practices. Organizations are increasingly adopting zero trust models, using AI and ML for security, and implementing cloud-native security solutions.
These trends are helping organizations to improve their security posture and stay ahead of the curve in the fight against cybercrime.
– Provide examples of real-world use cases where advanced cloud networking security protocols have helped organizations achieve compliance.
Advanced cloud networking security protocols have helped organizations achieve compliance in various ways. For example, organizations in the healthcare industry can use these protocols to meet the requirements of the Health Insurance Portability and Accountability Act (HIPAA). HIPAA requires healthcare providers to protect the privacy and security of patient health information.
Advanced cloud networking security protocols can help organizations meet these requirements by encrypting data, authenticating users, and preventing unauthorized access to data.
Real-World Use Case
One real-world example of how advanced cloud networking security protocols have helped organizations achieve compliance is the case of a large healthcare provider. The healthcare provider was required to meet the requirements of HIPAA. To do so, the healthcare provider implemented a cloud-based electronic health records (EHR) system.
The EHR system was protected by a variety of advanced cloud networking security protocols, including encryption, authentication, and access control. These protocols helped the healthcare provider to meet the requirements of HIPAA and protect the privacy and security of patient health information.
Future of Advanced Cloud Networking Security Protocols
The future of advanced cloud networking security protocols is promising, with several potential advancements and innovations on the horizon. These protocols will continue to evolve to meet the evolving security challenges of the cloud, including the increasing sophistication of cyberattacks, the growing adoption of cloud services, and the increasing amount of sensitive data stored in the cloud.One
of the most significant trends in the future of advanced cloud networking security protocols is the adoption of artificial intelligence (AI) and machine learning (ML). AI and ML can be used to automate many of the tasks associated with network security, such as detecting and responding to threats.
This can free up security professionals to focus on more strategic tasks, such as developing and implementing security policies.Another trend in the future of advanced cloud networking security protocols is the adoption of blockchain technology. Blockchain can be used to create a secure and tamper-proof record of network activity.
This can help organizations to track and investigate security incidents, and to ensure that their networks are compliant with security regulations.In addition to these specific trends, the future of advanced cloud networking security protocols is also likely to be shaped by the following general trends:
- The increasing adoption of cloud services
- The growing amount of sensitive data stored in the cloud
- The increasing sophistication of cyberattacks
These trends will continue to drive the development of new and innovative security protocols, as organizations seek to protect their networks and data from increasingly sophisticated threats.
Cloud Networking Security Best Practices
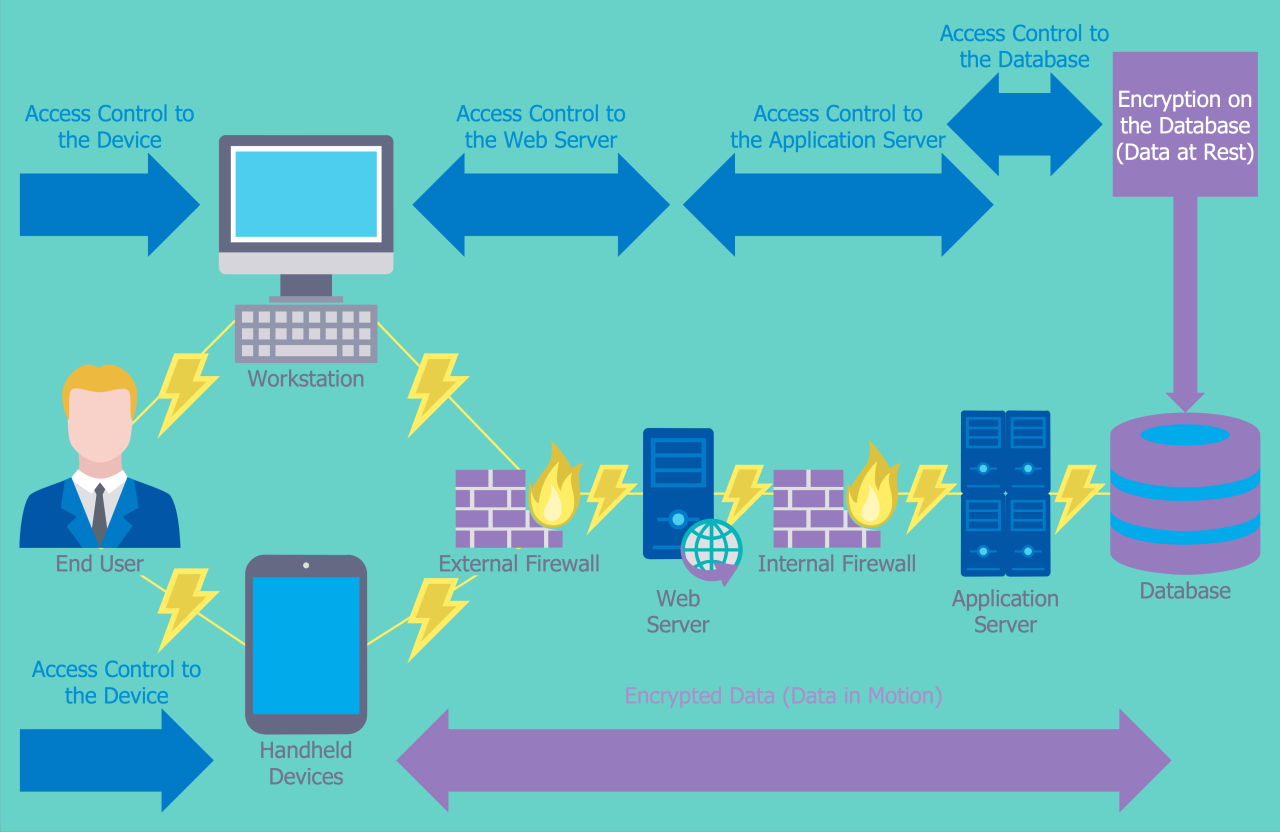
Implementing advanced cloud networking security protocols is crucial for safeguarding your cloud infrastructure and data. By adhering to best practices, organizations can strengthen their security posture and minimize the risk of security breaches.
Here are some key best practices for implementing and managing advanced cloud networking security protocols:
Network Segmentation
- Divide your cloud network into smaller, isolated segments to limit the spread of potential threats.
- Implement firewalls and access control lists (ACLs) to control traffic flow between segments.
Data Encryption
- Encrypt all sensitive data, both at rest and in transit, to protect it from unauthorized access.
- Use strong encryption algorithms and key management practices to ensure data confidentiality.
Access Control
- Implement strong access control mechanisms, such as multi-factor authentication and role-based access control (RBAC).
- Regularly review and update user permissions to prevent unauthorized access to sensitive resources.
Vulnerability Management
- Regularly scan your cloud network for vulnerabilities and patch any identified issues promptly.
- Use automated vulnerability management tools to streamline the process and ensure timely patching.
Incident Response
- Develop and implement a comprehensive incident response plan to guide your response to security breaches.
- Establish clear roles and responsibilities for incident handling and communication.
Continuous Monitoring
- Continuously monitor your cloud network for suspicious activity and security events.
- Use security information and event management (SIEM) tools to collect and analyze logs and alerts.
Advanced Cloud Networking Security Tools
Implementing robust security measures is crucial for protecting cloud networking environments. Advanced cloud networking security tools offer comprehensive protection against a wide range of threats, enabling organizations to safeguard their sensitive data and applications.
Cloud Firewalls
Cloud firewalls provide a first line of defense against unauthorized access to cloud resources. They allow administrators to define firewall rules that control inbound and outbound traffic based on source IP addresses, destination IP addresses, ports, and protocols. Advanced cloud firewalls offer features such as stateful inspection, intrusion detection, and threat intelligence integration.
Intrusion Detection and Prevention Systems (IDS/IPS)
IDS/IPS systems monitor network traffic for suspicious activity and take action to prevent or mitigate attacks. IDS systems detect suspicious activity by analyzing traffic patterns and comparing them to known attack signatures. IPS systems go a step further by actively blocking or dropping malicious traffic.
Web Application Firewalls (WAFs)
WAFs protect web applications from attacks such as SQL injection, cross-site scripting, and DDoS attacks. They do this by inspecting HTTP traffic and blocking requests that contain malicious payloads or that violate security rules.
Distributed Denial of Service (DDoS) Protection
DDoS attacks overwhelm a target system with a flood of traffic, causing it to become unavailable. DDoS protection services mitigate these attacks by distributing traffic across multiple servers and filtering out malicious traffic.
Security Information and Event Management (SIEM)
SIEM systems collect and analyze security logs from multiple sources, providing a centralized view of security events. They can detect and alert on suspicious activity, enabling organizations to respond quickly to security incidents.
Cloud Access Security Brokers (CASBs)
CASBs provide visibility and control over cloud usage. They enforce security policies, monitor cloud activity, and protect sensitive data. CASBs can help organizations comply with data protection regulations and ensure that cloud usage is aligned with security best practices.
Cloud Security Incident Response: Advanced Cloud Networking Security Protocols
Advanced cloud networking security protocols play a critical role in cloud security incident response by providing organizations with enhanced visibility, detection, and response capabilities. These protocols enable organizations to monitor and analyze network traffic patterns, identify suspicious activity, and take immediate action to mitigate threats.
Real-Time Monitoring and Analysis
Advanced cloud networking security protocols allow organizations to monitor and analyze network traffic in real time. This enables security teams to detect and investigate potential security incidents as they occur, minimizing the risk of data breaches or other security compromises.
Automated Threat Detection
These protocols incorporate advanced threat detection algorithms that can automatically identify and flag suspicious activity, such as unauthorized access attempts, malware infections, or data exfiltration. By automating the threat detection process, organizations can significantly reduce the time and effort required to detect security incidents.
Rapid Response and Mitigation
Advanced cloud networking security protocols provide organizations with the ability to rapidly respond to and mitigate security incidents. By automating certain response actions, such as blocking malicious IP addresses or isolating infected systems, organizations can minimize the impact of security incidents and restore normal operations as quickly as possible.
Recommendations for Enhanced Incident Response
To enhance cloud security incident response capabilities, organizations should consider the following recommendations:* Implement a comprehensive cloud networking security solution that includes advanced security protocols.
- Regularly review and update security policies and procedures to ensure they align with industry best practices.
- Conduct regular security audits and penetration testing to identify and address potential vulnerabilities.
- Train security teams on the latest threat detection and response techniques.
- Establish clear communication channels with cloud service providers to facilitate rapid incident response.
Final Thoughts
By implementing advanced cloud networking security protocols, you can significantly improve the security of your cloud-based applications and data. These protocols provide a comprehensive range of security measures that can help you protect against a wide range of threats, including data breaches, malware, and DDoS attacks.